We are going through a digital revolution. In our day to day, life computers have become an essential accessory. Be it the simple one like the smartphone you use or the navigation system in your car. We have become dependent on them. Normally we give some input, the computer processes it and gives an output. But in IoT, the computer does not need human-machine or human-human interaction for every data it transfers.
What is IoT?
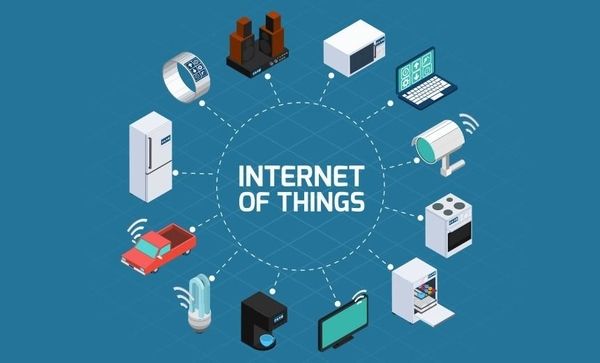
You must be thinking of what actually is IoT? It is a network of digital appliances such as computers, laptops, etc. connected together to impart data sharing between them. IoT does not require any kind of human to machine or machine to machine interaction for its fulfillment. All the devices which are connected to this technology are gifted with UIDs. An MIT graduate named Kevin Ashton first coined this term in his project. In the year 1999, he worked on a project named Gamble and Procter, which used RFIDs to identify the culprits.
How does IOT work?
There is a sure way in which IoT works. IoT is mainly blended with three parts :
- Sensor: This part consists of the primary input. To understand in simpler words, it is the part that the machine notices, e.g., when your car notifies you about the low amount of fuel in the tank, the part that notices the small amount of fuel is the sensor.
- Processor: It is the part that works like a brain and processes the data. The processor takes the data from the sensor and processes what the output should be. E.g., it is the part that makes the data like the amount of petrol in the tank sensed by the sensor and decides if it should notify you.
- Actuator: Now, these are the part that executes the output. It takes the instructions from the processor and acts likewise. E.g., the indicator light that notifies you about the low level of fuel is the actuator.
Scope of IoT
Day by day we are becoming more and more dependent on the machine. With the advancement of software development and the internet, it is becoming more and more common. And to think more wisely, wouldn’t it be cool if your car can interact with your house and tell it to warm up before you reach home or drive you to the fuckbuddy that you met on Free Meet N’ Fuck. The future of other technology interacting with dating applications or other services we use is interesting. Imagine if your umbrella gets the weather forecast and beeps itself to remind you about keeping it with you? There are billions of items or machines or software available for IoT. It has its application in every kind of industry. It is becoming easier to use with easily accessible WIFI networks. With some simple things, anyone can use IoT. You just need:
- A sensor to detect input time to time
- Software to look at the sensor data and process decisions
- A software to manage the operation of a device which includes more than one sensor
- And an internet connection to transmit and receive data.

With the increase in these things, the day is not away when IOT is going to be everywhere. Which also raises concerns about IOT cybersecurity. We will save this for another article, but it is a whole new area to consider. …